There’s an ever-evolving arms race between criminals who want to hack your website, and those who seek to stop them.
Most of the security measures we use work away in the background, without you needing to do anything. They’re very-much ‘unsung heroes’ – so we thought it only fair to give them some love in a post here!
This is partly a companion to our WordPress Security Guide, which covers everything that a WordPress user can do secure their website. But here, we’ll concentrate on what we do for everyone on our hosting platforms. Most of these security features apply to our Web Hosting, WordPress Hosting and Managed Hosting.
Web application firewall
What is a web application firewall (WAF)? An analogy might be a doorperson or bouncer at a nightclub. The WAF ensures that the right things are let in, and the wrong things are burnt to a crisp in a 1000-degree wall of flame ?.
It’s a shield for ‘web applications’. A web application could be anything involved with your website – most commonly the content management system – but it includes anything that might transmit data between the client (like the browser) to the server (your hosting). The things that transmit the data are often called ‘scripts’.
Criminal hackers can attempt to hijack these scripts and insert their own commands, using methods like SQL injection or cross-site scripting.
The firewall works by intercepting these attempts. We use ‘off the shelf’ sets of rules available to all, but supplement and enhance these by using our own filtering rules, created by our security experts. It’s like the security at the nightclub having access to your birth certificate and school reports…
It’s also important to note where this ‘filtering’ takes place. The WAF stops attacks and malicious uploads at the network edge. This is before the web application (e.g. WordPress) even executes. It’s like the bouncer stopping you before you even get in the queue.
That’s why you won’t ever hear about security breaches from 20i users.
Our autoscaling platform
“I thought your autoscaling was to do with sites that received spikes in traffic getting allocated as much multi-server hosting resources that they need, not security?” says my imaginary pet cat.
Well, Mr Fluffsome McTanglepaws would be right about the traffic, but it does have an impact on security too. Surges in traffic can be the result of malicious intent.
While you might be thinking of DDoS, server resources can be used up in other ways: an attempt to brute-force a password, for example.
On other web hosting – where websites are confined to the resources of single server – this can cause slowdown. A bot trying every variant of ‘pa55word’ in a form will use up a lot of processing power, so other sites on the same shared server can be affected.
Not so with 20i: if an attack that uses lots of resource takes place, our autoscaling tech will still scale with as much server resource as needed – until the attack is stopped by our other security measures. That resource isn’t confined to a single server. Other sites on the platform (as well as the site in question), won’t be slowed down.
StackProtect
StackProtect is a form CAPTCHA (which stands for ‘can’t you just look it up‘?). We cover it in detail here, but in a nutshell, it’s a way to prove you’re human. One of the main areas it’s used is on WordPress_admin login pages – but it protects any web apps that need to have secure logins.
We use reCAPTCHA version 3, which uses complex behavioural tests to ensure that you’re not one of our Plastic Pals Who Are Fun To Be With. So there’s no need squint at a badly-written number or word. Or spend ages trying to work out what American fire hydrants look like.
StackProtect is a way to protect against bots that might try to guess your password through high-speed ‘brute force’, by trying all the common ones. It’s uses a JavaScript challenge to filter out bad bots vs real browsers.

(It’s called ‘StackProtect’ – as opposed to ’20i Protect’ or similar – because all our services that are used by 20i Resellers are white-label hosting, so a Reseller doesn’t have to mention 20i if they don’t want-to).
Daily malware scans
While you can carry out a malware scan whenever you like, we also scan all sites hosted with us daily.

Should we detect potential malware, you’ll receive a notification by email and when you log in to My20i. You’ll get a report which will give you advice on how to fix or remove it. If you’re unsure about what to do, you can always rely on our Support Team, who are there for you all-day, every day.
Network defences
To go back to the security on a nightclub analogy (sorry), these network defences are like the bouncer knowing the address of those in the queue – and banning those from the ‘wrong side of the tracks’.
Suspicious IP address and networks are automatically routed to different web servers to keep traffic and load away from standard web servers. If they’re not just suspicious, but known to be proper naughty little scamps, we can outright ban IP addresses or ranges of IP addresses. They’re blocked at the network edge.
We use publicly-available reputation scores to find this out. We also learn from problems we encounter, so we have our own rules too.
DIY defences
These are similar to the above, but give you (and your customers, if you’re a Reseller) the option to make your own security rules. You can block individual IP addresses, ranges and block by country too.
With live data from our free CDN, you can see where people are visiting you from and make changes on the fly. It’s made simple with rules like ‘block all, except:’ and ‘allow all, except:’.
DDoS protection
Distributed Denial of Service (DDoS) attacks are the bane of site owners and their web hosts. Script kiddies in their bedrooms can take down large corporates by flooding their servers with requests. While that’s great for democratisation of crime, it’s not so great for business.
So we use Enterprise-grade DDoS protection on our servers, both in-house and with upstream service providers. It’s best you can get.
When I started at 20i I was surprised to discover that we get DDoS attacks on a daily basis! But as a customer, you don’t hear about it, as once they’re detected, the ‘bad’ traffic is blocked. The ‘good’ traffic – your customers, for example – are still allowed through our defences.
Free SSL certificates
We ❤️ Let’s Encrypt. No, not in that way.
But SSL certs (or if you want to be pedantic – and I always do – x509 TLS certs) are one of the best things that have happened to the web. They encrypt the data flowing between the browser and the server, so it’s a lot more difficult to intercept your personal data.
Google’s encouragement to use them (by virtue of ranking boosts for those sites that have them), means that it’s a good idea for any site to have one. We can provide them without any cost, and it’s a simple matter of a single click to give your website the ‘HTTPS’ treatment.
Two-factor authentication
Two-factor authentication (2FA) is one of the best ways to protect your security. Even if someone knows or has guessed your pa$$word, it adds an extra level security that criminals find difficult to bypass.
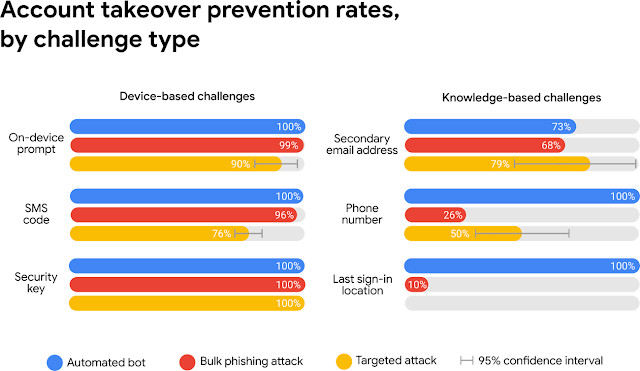
How device-based challenges work better than knowledge-based ones. Credit: Google
If you’re unfamiliar with it: it’s the thing where you’ll need to get an extra code when logging-in, sent to you by text on your phone or though using an authenticator app. The code is time-limited.
As you may be logging in on a different device (like your home PC), it provides that all-important ‘air gap’ between the device – which could have been compromised – and the criminals who want to steal your details.
At 20i you can use 2FA when you log in to our control panel, My20i, while Resellers’ customers have the same option with StackCP. SSH – which is used to issue commands to a server, like your website files – can also use 2FA and security keys. It’s fast and easy to set up – as I’m sure you’d expect from us.
I’m always amazed that so many other web hosts don’t provide this simple feature. If you’re shopping for hosting, it’s a good indication of how seriously they take their security.
WordPress Tools
For WordPress users, WordPress Tools – included with all WP hosting – offers some extra safeguards. You don’t have to log in WordPress_admin: you can manage users, plugin and theme versions all from My20i. So your password is less likely to be compromised.

Another great feature is our WordPress Checksum Report. This checks your version of WordPress against the ‘correct’ version in WordPress’ repository.
A checksum works by applying an algorithm to the data which ‘scrambles’ it. The resulting code is then sent to the recipient who also knows the algorithm. If the scrambled version doesn’t match, then it’s possible that there’s a difference in the data. For WordPress, this often means that there’s been some pesky hackery at work, and we’ll let you know.
A good illustration is like when you take a hammer to your expensive laptop. It’s very cathartic.
If you knew the weight of the hammer, the strength and angles of the blows, and have infinite patience and magic glue, you could probably reassemble it – in the same way a checksum algorithm does. If it didn’t work, or if after you’ve reassembled it, the keyboard has an extra letter ‘K’, then there might be something fishy going on.
The usual suspects
If you want to transfer files to our servers, we make it easy for you – but difficult for cybercriminals.
Some common avenues for nefarious access attempts are made much more difficult with 20i. FTP, Remote MySQL and SSH are denied as standard and can only be enabled after authentication through our control panel. And hopefully you’ll have protected that control panel with a strong password and 2FA!

Speaking of strong passwords – we also have a strong password generator in My20i, so you don’t have to use a separate app.
Another way to compromise your security is if the permissions on your files are incorrect. Our File Permissions Checker will scan all the permissions on your website files. If any are different to what we recommend, we’ll let you know and we can change them for you, automatically.
The most robust hosting platform
Our platform is the toughest around, so even in the unlikely event that there was ever some kind of security breach, it won’t affect our customers’ sites.
It’s designed without a single point of failure. So if there was a hardware, software or network failure, failover will happen, using redundant systems and hardware.
While this will keep websites live and running, it has the extra advantage of protecting against data loss.
Set roles for our socially-distanced servers
Instead of bunging everything on one server – which can be inefficient as well as insecure – our servers have different roles. Email servers run email, MySQL servers just run MySQL, storage just stores and web servers…serve websites.
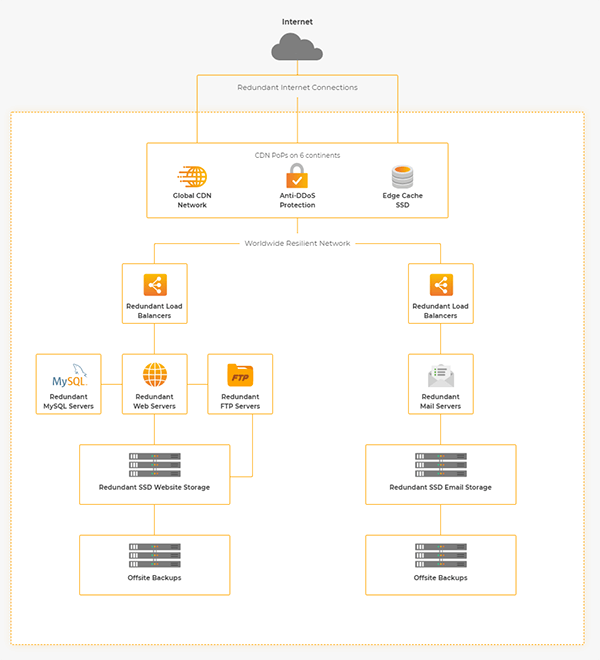
So even in the worst-case scenario and your site has been compromised, the attacker can’t delete log files to cover their tracks or read your email. The data is on secure, physically-separate machines.
While our servers can talk to each other over a fast 10 GB network, they aren’t in the same room. Your backups are kept at locations remote from our main servers: different data centres.
All these data centres have redundant emergency power supplies in case we forget to pay our electric bill or whatever. In the apocalyptic event that might cause all of our data centres to fail, I doubt that your website would be your top priority…
You’re not getting in
We only operate out of ISO 27001-accredited data centres. This is an international standard for information security.
What this means in part is that we can now get back to bouncer/doorperson analogy – but in real life! It really is difficult to get in to one of our data centres.
Would-be Elliot Aldersons wouldn’t make it past the front gate.

They have 24/7 security guards who enforce strict rules, even if they know you. That means photo IDs, CCTV and strict access controls.
It’s up to you now
Of course, we can’t guarantee that your site will be 100% secure. No one can. There are still avenues of attack that we can’t control: like someone knowing your password.
But we’ve done as much as we can – and more than anyone else – to secure your website when it’s hosted with us. And we continue to update and improve things all the time. Furthermore, we’re committed to make all our security measures included for no extra charge: even if it’s free hosting!
You’ve got the best-possible security, and as long you’re careful, your website is as safe as it can be when you’re with 20i.







Thanks for the blueprint to all your security measures. Now that I know what I’m up against I shall be there soon to wreak havoc upon your systems and create the biggest nightmare you’ve never heard of yet.. Haha, just joking of course.
It’s great to know 20i does all it can to protect their systems and customers. But I hope anyone who reads this post doesn’t think they need to worry too much about their own website security. I’m actually going to use all the info in your post and highlight it on my own site now as I think top notch web security is a seller, especially if it’s done alongside real-life horror stories which I’ll go do some research on now.